Adding a default route
As we saw in previous post https://old.smenode.com/data-plane-interfaces/ now in firewall 1 we have one interface we are going use for management purposes on a management network, and we have 3, one goes up to service provider, one connects to internal network and one connects to DMZ. They are keeping use the part of the data plane for forwarding user traffic and back in port between networks. Our next step is to add a default route so if this firewall needs to reach any network besides the four of this directly connected to, it knows how to do exactly that.
In preparation for a user who’s trying to access maybe a DNS server in the internet or trying to access a website on the internet, if the packet comes in to the firewall (1) and that packet destined for example to 8.8.8.8 which is a DNS server from Google, this firewall currently can’t do it and has no idea how to forward beyond those locally connected networks. So, if we added the default route we can say dear Mr. firewall 1 if you don’t have a more explicit or exact route in routing table for 8.8.8.8 the last afford should be using the default route and send it to the next hob address associate with your default route, in our case we are going to use 23.1.2.1 network.
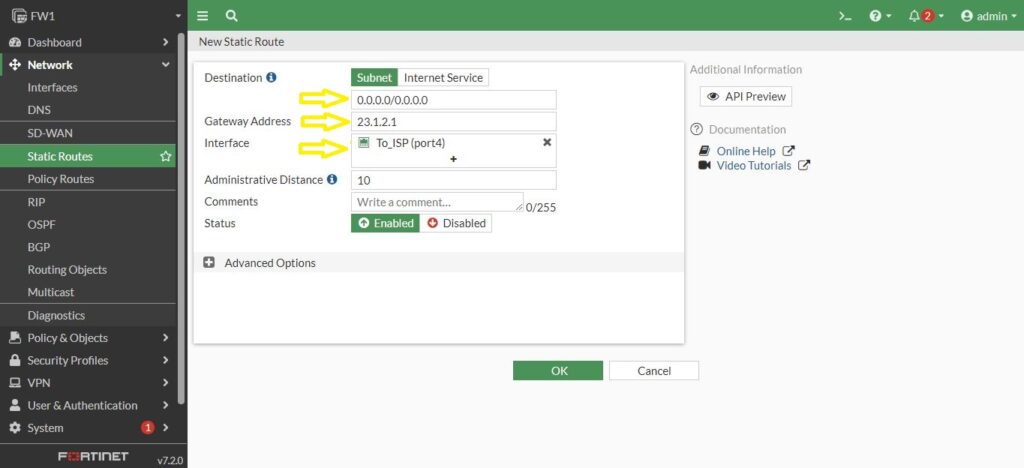
[arm_form id=”102″ form_position=”center” assign_default_plan=”0″ logged_in_message=”You are already logged in.”]So, let’s go to firewall 1, in the Network section, we have a Static Route option. After click on it, we create a brand-new static route. It is not going to be any route, it is a default route, the 0.0.0.0/0.0.0.0 is how we represent as default route in IPv4 and the Gateway Address use as default route is specific 23.1.2.1 so it is directly connected via Port4, and that’s why by default is selected port4 to reach that next hob.
Maybe we have different default routes for different sources in any event, for example routes for OSPF or another routing protocols, the way a firewall chooses which one put in the routing table is based on Administrative Distance, and in AD the lower score wins. So, when comes down to multiple routing sources for the same exact routes, in this example default route, routing source has the lowest administrative distance is going the way. For example if our default route has 10 and another ospf route has 110 , the default route which has 10 is chosen by firewall.
Routing Table
And let’s go check out routing, so go back to Dashboard and under that, look on the Network.
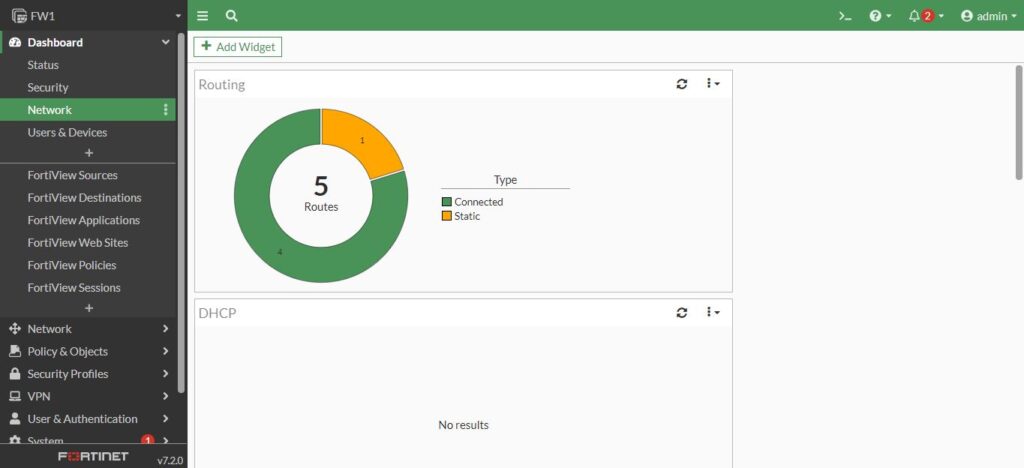
It shows we have 5 routes, 4 directly connected routes and 1 static route which is our default route. And with click on it expands the details, including routing table.
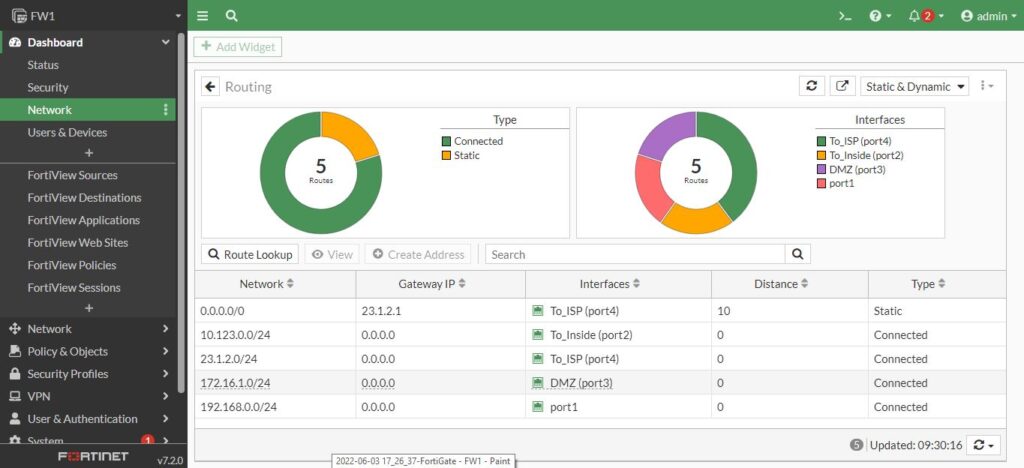
So, the first one in the routing table is our default route, and the four ones is the connected routes as well.
Another way of looking at routing table on this firewall from the command line would be good. Open the CLI and with below syntax:
FW1 # get router info routing-table all
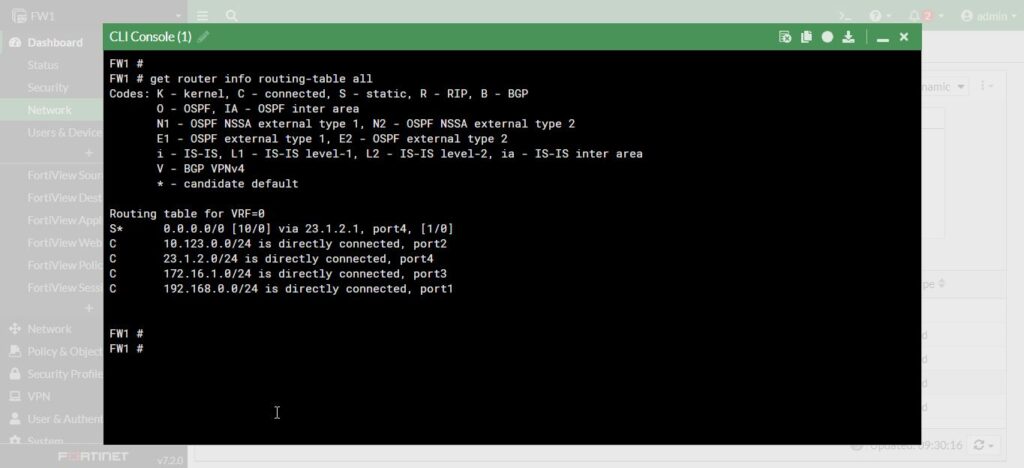
So that’s showing us the routing table, including four connected routes and the static default route we just configured.
And if we go back to the Network and Static Route. And click on our default route, once again we have an option to edit that at the CLI.
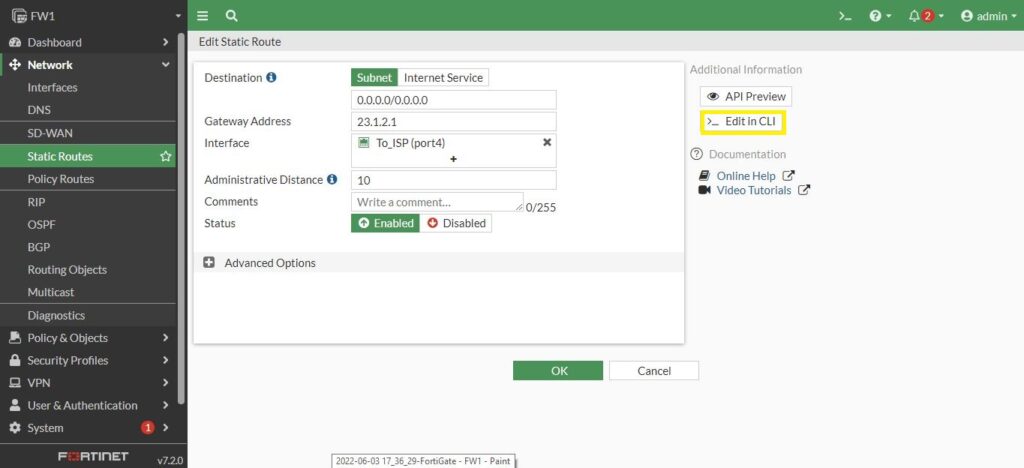
We can see the configuration of default route in the CLI. Again it shows the convenience Fortinet has placed in the fortigate firewall at the cli.
Test the connection
Now we are going to test the connection of the firewall to the internet. In the command line using the command execute and then traceroute the 8.8.8.8:
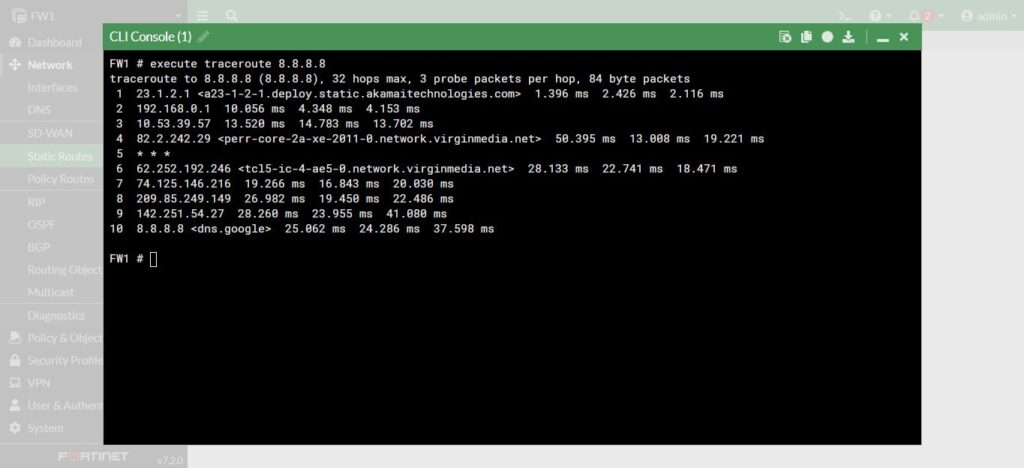
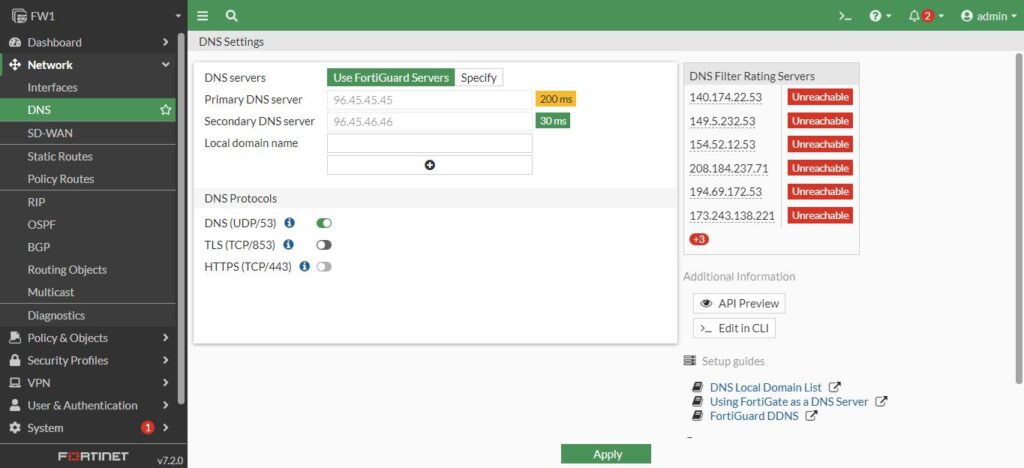
So, you can see, the first one is our 23.1.2.1 default route and the last one is 8.8.8.8. <dns.google>. It shows our dns is working, if you take a look at the default configuration on the firewall under the Network, we have DNS and then the DNS has two preconfigure addresses using for dns. We can change to the specify dns servers with Specify option or just use the default which provided for us either way is great.
In the next post https://old.smenode.com/fortinet/verify-the-data-plane/ we will put a PC behind the firewall and on that 10.123 network and verify that PC can get access through firewall 1, through the internet.
