SSH or Secure Shell is a secure protocol for remote communication between systems and servers. This protocol is an alternative to Telnet, which has security and encryption mechanisms. This article will discuss 7 tips to secure the SSH protocol.
In the past, the Telnet protocol was used to establish remote communication, execute commands, and manage systems and servers. Still, since this protocol did not support encryption and transmitted data in plain text between systems, it was considered an excellent risk for organizations. Note that when a MITM attack takes place, or a person can eavesdrop on network data, he can easily see Username and Password and even their commands and responses.
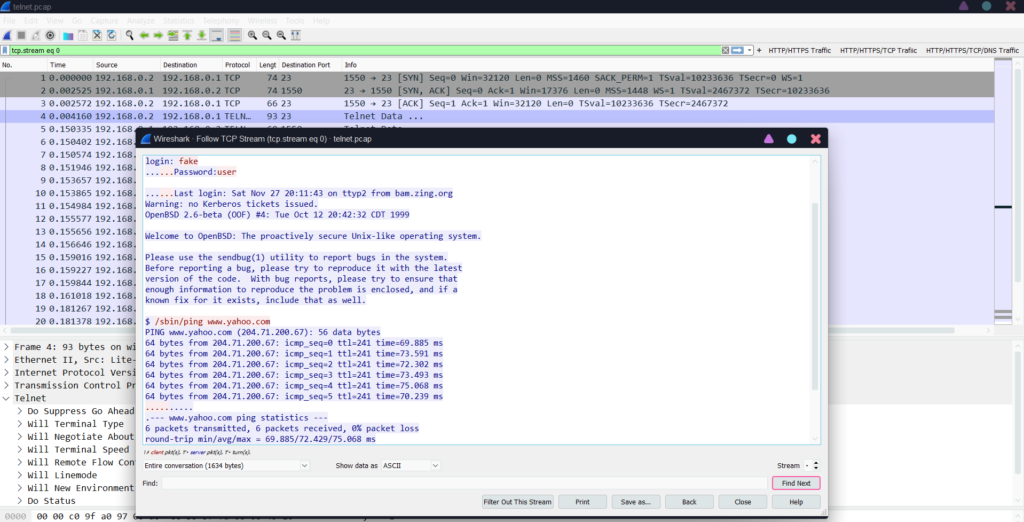
SSH vs Telnet Packet Data
For example, the image below is a Telnet packet, which can be readily displayed with Wireshark after opening the Username and Password sections.
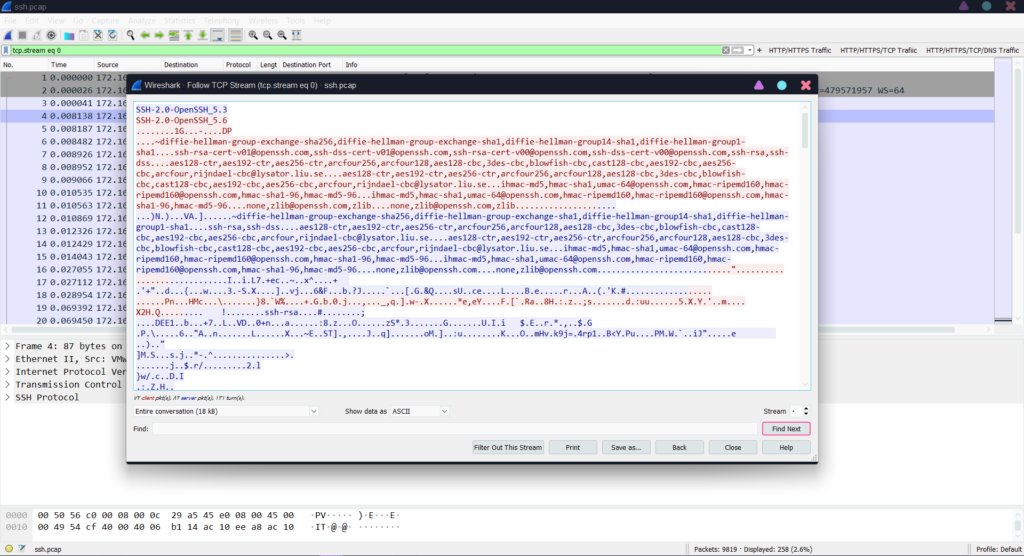
Now, in the picture below, we see an SSH packet that is fully encrypted, and without having the key, we cannot see the information and data inside the SSH packet.
Introducing to SSH attacks
In this section, we will introduce and check the most used attacks by hackers towards the SSH protocol, that these attacks are independent of recorded vulnerabilities and CVEs.
You may be asked if SSH is not a secure protocol? So why are we talking about SSH attacks here? The answer to your question is that SSH is safe, but it is safe compared to the Telnet protocol and the new security mechanisms it has. Still, it requires security configuration and proper setup considering security points.
Attack 1 – BruteForce
One of the most common attacks among hackers on the SSH protocol is the BruteForce attack. With many usernames and passwords, this attack tries to achieve results by testing these usernames and passwords several times. Sometimes there are situations where this attack is performed only on the Password part, and knowing the Username, the attacker tries to guess and test many Passwords. This attack is effective when employees use straightforward and predictable passwords without considering the tips for writing passwords.
Note: A safe password must contain English lowercase, and uppercase characters along with special characters such as & / * % $ #, etc, and the length of this password must be at least 16 characters or more. Also, you can use the PaasowrdGenerator website to have a secure password and create a secure password by specifying the length of the password and using unique, small, and large characters.
Attack 2 – Spray And Pray
This attack happens when a group of threat actors intends to test many usernames and passwords on several servers where SSH is enabled and maybe one of the answers on the servers. If this attack is successful, it will be due to employees not knowing how to write secure passwords.
6 security tips for securing the SSH protocol
Disable Root Login
This point is one of the oldest and most important things that should be considered for SSH security. When we start SSH, it is possible to access the root user by default. This issue can be very dangerous because the root application has full access to all system parts. Logging in to the Root user should be disabled in the SSH configuration. Even if people use strong passwords, it is suggested to disable this access, and if the user wants to have Root access, only “su” and “sudo” commands are available.
Change the default ssh port
Another important tip in configuring SSH is to change its default port (22) to another port so that the attacker cannot quickly identify the port related to SSH and start his attack.
Set a limit on the number of passwords entered
Limiting the passwords tried by the attacker is an essential issue in preventing BruteForce. In this method, we will configure SSH so that the attacker or any other person will not be able to enter a new password, and his access will be blocked if he enters the wrong password as many times as you specify.
Set Notification to monitor SSH Login
One of the tips that can help monitor SSH logins, especially root logins, is to create a script in the system for when a person accesses the root user. This script can be such that if someone enters the root user, an email will be sent to you as a warning.
Set Timeout Interval
When we configure this feature, SSH sessions that are not used will be closed automatically. For example, an SSH session has been active on our server since three days ago but is not being used. Using this method, we can specify that if an SSH session has no activity after, for example, 2 minutes, close it.
Set Passwordless Login
Note that in this method, we do not use a password. No matter how strong passwords are, they cannot resist BruteForce attacks. For this reason, in the Passwordless Login method, we use an SSH Key to log in to the system, and this process is much faster, simpler, and safer than logging in with a password.
Disabling accounts with empty passwords
In SSH, we can create users who do not have passwords and log in easily through them. This issue is very dangerous and must be disabled by system administrators of accounts without passwords.
Read More: Introducing To The 13 Malware Analysis Tools
