In this article, we are going to talk about the DeepBlueCli tool for Threat Hunting in Windows via Event Viewer (Event Log). This powershell script can analyze various events in the Event Log, including Sysmon, Application, Security, etc.
What Is DeepBlueCli?
DeepBlueCli is a PowerShell-based tool used to detect and detect threats. This tool is provided by SANS Security Institute. DeepBlueCli can detect threats and show us dangerous events through Event Log in Windows. This tool can analyze both live files and pre-saved files.
Note: DeepBlueCli is faster for pre-saved files.
DeepBlueCli Installation
In this part of the article, we first install DeepBlueCli on our Windows system and then analyze some Evtx files through DeepBlueCli. To install DeepBlueCli, you need to download this tool from Github and then extract it from Zip mode.
- DeepBlueCli GitHub: https://github.com/sans-blue-team/DeepBlueCLI
Now go to the DeepBlueCli folder via Powershell and run the DeepBlueCli.ps1 file
- Note: If you received this error:
.\DeepBlue.ps1 : File .\DeepBlue.ps1 cannot be loaded because running scripts is disabled on this system. Use the following command to fix the error.
Set-ExecutionPolicy BypassDeepBlueCli Command Usage
Process local Windows security event log (Powershell need run as Admin)
.\DeepBlue.ps1 -log security
or
.\DeepBlue.ps1 -log systemProcess ETVX File:
.\DeepBlue.ps1 .\evtx\new-user-security.evtxThreat Hunting With DeepBlueCli
1 Scenario – EventLog Cleared & Restarted
In this scenario we analyze an Evtx file (in the Evtx folder) called “disablestop-eventlog.evtx” via DeepBlueCli.
To do this, we need to enter the DeepBlueCli.ps1 command with the path to the Evtx file.
.\DeepBlue.ps1 .\evtx\disablestop-eventlog.evtx
In the output above we see that EventLog has been cleared and then restarted. This is suspicious behavior.
2 Scenario
In this scenario, we see the Metasploit behaviors that execute the getsystem command.
.\DeepBlue.ps1 .\evtx\metasploit-psexec-native-target-security.evtx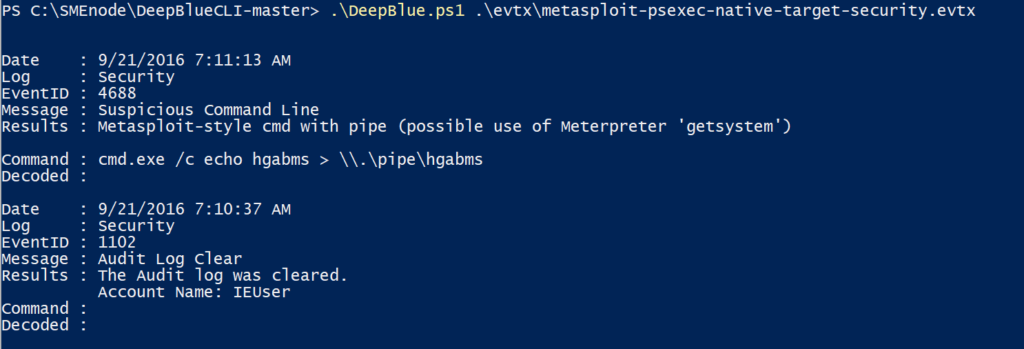
This command uses three techniques to enhance user privilege to system privilege. Two of these techniques include Named Pipe Impersonation and the last technique involves Token Duplication. The “Named Pipe Impersonation” technique is used here and this story has been identified by DeepBlueCli.
meterpreter > getsystem -h
Usage: getsystem [options]
Attempt to elevate your privilege to that of local system.
OPTIONS:
-h Help Banner.
-t The technique to use. (Default to '0').
0 : All techniques available
1 : Service - Named Pipe Impersonation (In Memory/Admin)
2 : Service - Named Pipe Impersonation (Dropper/Admin)
3 : Service - Token Duplication (In Memory/Admin)
Note: Use the Out-GridView command to display the DeepBlueCli output in a GUI window.
.\DeepBlue.ps1 .\evtx\eventlog-dac.evtx | Out-GridView 
Read More: What Is Azure Sentinel? Cloud-Native SIEM

1 Comment