The process of Incidents Response is important and its accurate and principled performance is more important. Therefore, this process, like other processes in the field of security, has special tools that make the process of Incident Response easier and faster.
In this article, we are going to introduce the Incidents Response process and introduce 5 of the best disaster response tools that are provided for free and open-source.
What Are The Phases of Incidents Response?
From the perspective of SANS, disaster response phases are divided into 6 different phases, which are as follows:
Phase 1 – Prepare: In this phase, we begin to create a disaster response team, prepare the environment, inform the organization about cyberattacks on employees of the organization, review their assets and risks (a kind of Threat Modeling), create security policies And assess the risks and risks of the organization’s environment
Phase 2 – Identity: In this phase, which is known as identification, our goal is to examine the systems and have monitoring and monitoring on them to detect and identify malicious behaviors and various habits. In this phase, we must hack real-time Identify them and classify them and check their severity
Phase 3 – Contain: In this step, we use methods that temporarily and short-termly separate systems infected with threats and attacks from other uninfected systems so that we can more safely process security and troubleshoot. And perform the patch operations and then re-enter it into the main network
Phase 4 – Eradicate: In this step, we must identify the root cause of the attack and the incident, eliminate the existing problems and malware, and take various defensive measures to prevent the recurrence of this type of attack.
Phase 5 – Recover: In this phase, recover the systems and apply the security configurations and defensive measures to prevent further attacks.
Phase 6: Learn: In this phase, complete reports and documents should be prepared from the description of the incident and its details, and it should be examined what process should be done to prevent the recurrence of such attacks, which will improve the process of Incident Response.
What Is Incidents Response Tools?
When we want to use disaster response tools, there are many tools in front of us that we can use that are both monetary and open source, but in situations where we want to be involved. Choose the two categories of non-free and open source tools, choose one better, choose open source because they are free, and in choosing the terms, these tools are better than their similar monetary tools, or they are level or complement the other tools. In this article, we are going to introduce and review 5 of the best open-source tools for disaster response.
1: Cyber 360
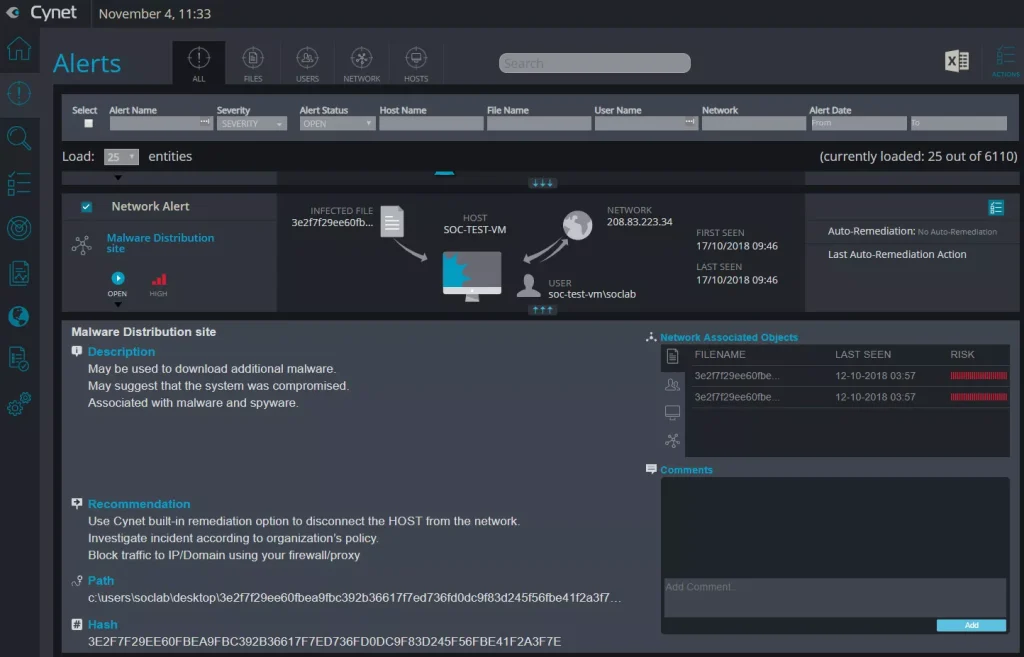
Cynet 360 can not be used in the incident response process alone, as it is a complete set of security features and remedies to deal with damaged and infected hosts. This platform can handle malicious files, unknown and unusual traffic from C&C servers, and damaged user accounts.
When IR or Incident Response teams use Cynet 360, they can monitor their environment in less than an hour, and it will take just one click to compensate for the attacks. To use Cynet 360 for free, you must first become a Cynet Partner. In addition, Cynet provides teams with 24-hour and 7-hour teams to respond to attacks and organizations that have been attacked.
2: AlienVault OSSIM
AlienVault OSSIM is a widely-used open source SIEM that allows analysts to have a great view of their systems and processes. This tool can do this process for us by providing various reports and information from other security tools.

3: Volatility Memory Forensic Tools
Volatility is a free open source tool for performing digital criminology and autopsy on the Memory platform, which is known as one of the best tools in the field of Memory forensics.

4: SANS SIFT Workstation SIFT
SIFT Workstation is an operating system provided by the SANS Institute, whose main activity and performance is in the field of forensics, through which we can use a wide range of tools in the field of forensics This operating system is free and based on Ubuntu or we can easily download and run it as a VMware Appliance.

5: Cyphon – IR Platform
Cyphon provides many tools for collecting, processing, and testing events that collect data from a variety of sources, including logs, APIs, and emails to make analysis easier.

